Cybersecurity Best Practices
Cybersecurity resources, best practices, and tips to help our clients protect their firms from increasing and evolving cyber threats, including ransomware attacks.
Best practices and tips

Password Strength Best Practices
Passwords are the most common method of authentication, but remembering a unique password for each account you have can be a pain. Here are ACA Aponix's best practices for creating and managing passwords to help protect your accounts from a cyber-attack.
- Cybersecurity
- Cybersecurity Resources
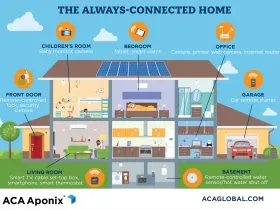
Protecting Your Home's Smart Devices
Our homes are becoming increasingly connected to the outside world through "smart" devices, which work together over your Wi-Fi network to make your home more comfortable, safe, and convenient. Common smart devices include thermostats, televisions, light bulbs, and surveillance systems.
- Cybersecurity
- Cybersecurity Resources

Protecting Your Online Identity
As cyber security attacks continue to increase in frequency and complexity alongside evolving technologies, the COVID-19 pandemic, and remote work and school, it is essential to prioritize protecting your identity online. Here are some ways you can control the amount of personal information that is available online.
- Cybersecurity
- Cybersecurity Resources

Talking to Your Family and Friends About Cybersecurity
The recent increase in high-profile cyber incidents have put millions of people around the world at risk for identity theft and other cyber-crimes. This blog post contains tips and information you can share with your family and friends about staying safe online.
- Cybersecurity
- Cybersecurity Resources

Ransomware 101 Part 2: How to Prevent and Detect a Ransomware Attack
Our Ransomware 101 blog series addresses multiple aspects of the ransomware issue, including what you should know and what you should do to protect your firm, your clients, and your finances. In part one, we discussed the evolving and growing threat of ransomware. In this article (part two), we’ll provide a framework for what your organization can do to prevent and detect ransomware attacks.
- Cybersecurity
- Cybersecurity Resources

Protecting Your Business as Offices Reopen: A Seven Step Cybersecurity Action Plan for Physical and Hybrid Work Environments
ACA Aponix’s cybersecurity experts have developed the following action plan to help your firm review, revise, and implement a strong cyber program that will help protect your firm against reputational and financial damage as well as meet regulatory obligations, no matter what type of work model you’re employing.
- Cybersecurity
- Cybersecurity Resources