When Push Comes to Breach: Hackers Use Push Notifications to Bypass MFA
From tracking packages and meal delivery service to approving logins to your accounts, push notifications play a vital role in the user experience. Not only can vendors send messages directly to your fingertips, push notifications in multifactor authentication (MFA) implementation allow users to protect themselves and impede cybercriminals. For the end user, it is no secret that less is more (more convenient, that is). With the simple touch of a button, MFA push notifications allow a user to feel they achieve “more” security with “less” effort and time (saving on average 13 minutes annually over other MFA implementation methods).
However, such ubiquity comes with evolving risk. While they are an effective and widely accessible method of security, users should still exercise caution when approving push notifications. Cybercriminals’ ever-growing hacking portfolio now includes the misappropriation of push notifications to bypass MFA—without needing access to a victim’s device yet with their “consent”.
In this article, we will:
- Review the background of MFA as it relates to push notifications
- Summarize what the push notification "malvertising" exploit looks like
- List immediate actions to take if you fall victim
- Discuss preventative measures
Background: a quick review
What to Know: What is MFA, and how does it relate to push notifications?
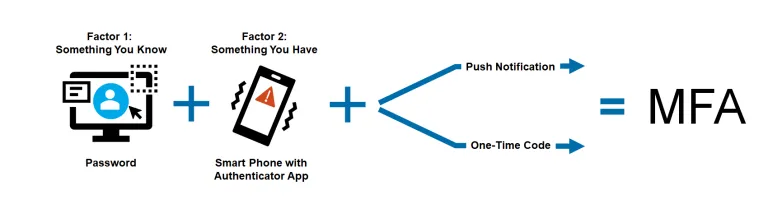
MFA is a method of verification that uses more than one step to prove your identity when you signing into accounts. These steps use multiple “factors” that are unique to the individual. One of the most common factors is “something you have”.
For example, you “have” a smartphone. One implementation of MFA utilizing a smartphone is the use of an authenticator app (such as Microsoft Authenticator and LastPass Authenticator). The authenticator app is a software token used to prove identification. Authenticator apps can be programmed to provide a user with one of two different verification methods:
- A push notification with buttons to either approve or deny login
- A one-time code to enter when prompted on the login screen
The login attempt cannot continue without user input because hackers do not have access to the device. However, that does not stop them from finding other ways to bypass these security measures.
In this article, we focus on the use of push notifications and their emerging risk.
Exploit summary: spammed into submission
What to Expect: Cybercriminals will spam users with a torrent of MFA push notifications during an attempt to compromise their accounts.
The cyber-espionage group behind the infamous SolarWinds supply chain attack, Nobelium, has used this exploit recently after compromising usernames and passwords. Nobelium continuously logged into the compromised accounts until users approved the login, thereby bypassing MFA with users’ “consent”. They even went as far as to use IP proxies in the same geographical areas as the victims to further lower their guard.
The hackers goal is to achieve push notification approval through one of the following methods:
- Tricking a user into thinking the push notifications are safe and just the result of a bug so they will validate the login attempt.
- Annoying a user until they approve a push notification to get them to stop.
- Waiting for a user to accidentally approve one of the push notifications in the swarm.
Exploit resolution: actions for victims
How to Mitigate: If you receive an MFA push notification randomly, do not approve it, even if the notifications become distracting or bothersome.
Instead, deny them and work patiently through the spam. The irritation of the inconvenience is not as long-lasting as the effects of a breach. To mitigate an ongoing threat:
- Trigger a password reset (click here for ACA Aponix’s guidance on password reset best practices).
- Change your account security questions.
- If applicable, alert your IT team to the suspicious activity.
- If possible, report your compromised accounts to their respective vendors.
Exploit preclusion: preventative measures
How to Prevent: Weigh the risk and practice good cyber hygiene with your accounts.
The ideal solution to averting this scam is to disable push notifications; however, given their prevalence and convenience, this is not always a viable option. In these instances:
- Do not let approving push notifications become “second nature.” Always try to be cognizant, avoid falling into routine, and never place 100% of your trust in any given push notification that you believe are safe. Threat actors want to capitalize on your trust and habits.
- Invest in educating your employees on MFA and its emerging risk, such as the one discussed in this article. Education is a critical line of defense.
In instances where your organization is considering MFA push notifications, evaluate the risk of their potential exploitation and implement strategically. Where your most critical enterprise information resides, consider other secure methods of MFA implementation, such as:
- Authenticator apps with push notifications disabled, instead requiring passwordless sign-in or passcode validation.
- Fast Identity Online 2 (FIDO2) security key.
- Software/hardware Open Authentication (OATH) token.
Where you currently use push notifications as part of MFA (either day-to-day life or as part of an organization-wide policy), take the following actions to prevent cybercriminals from compromising other common factors to prevent misuse:
- Do not share account credentials with others.
- Keep passwords long (15+ characters), complex, and unique after each password change. Never reuse passwords.
- Never dictate email or SMS codes to others.
ACA guidance
It is important to remember that MFA is arguably the most critical cyber defense an end user can deploy. With the emergence of this exploit, firms should use heightened scrutiny when implementing push notifications in the future as well as evaluate where in the firm, if at all, push notifications pose a risk. Ask yourself, is the risk of user error incapacitating enough that push notifications should be exchanged for another method of MFA?
In addition to the guidance outlined above, ACA Aponix recommends that organizations:
- Educate employees on the importance of MFA as well as its emerging risks. Drive home the criticality of understanding this exploit and how to combat it.
- Turn on location for MFA push notifications. If the hackers do not use IP proxies and the location of the fraudulent login attempt does not match the victim’s, it is easier to identify as an attempted compromise.
- Formalize a password reset policy across the enterprise.
- Conduct vendor due diligence on their cloud providers to evaluate their data protection policies. Intrusions at cloud providers can pave the way to compromised credentials at their customers (that’s you).
How we help
ACA Aponix offers the following solutions that can help your financial institution develop, implement, and maintain the required information security program to make sure push notifications are safe:
- Risk Assessments and Regulatory Compliance Testing Services
- Threat intelligence, Phishing Testing, and Monitoring
- Payment and Fraud Risk Assessment Services
- Penetration Testing and Vulnerability Assessments
- Vendor Diligence and Management
- ACA Aponix's PortCo Defend™
- Operational Resilience and Governance


