Whaling Attacks: How to Respond When a C-Suite Executive is a Victim
Whaling is a targeted attack aimed at high-level executives, often those in the C-suite (CEO, CFO, CIO, etc.). According to a press release by HP, whaling is soon to become one of the most prominent forms of cyberattacks, especially with firms that operate in remote and hybrid work environments. In this article, we describe:
- Whaling attacks and their impact
- How to prepare C-Suite executives to not fall victim to whaling attacks
- What to do if an executive is a victim
What is a whaling attack?
Whaling attacks are often a form of spear-phishing, or a targeted phishing attack. While spear-phishing attacks are aimed at employees, whaling attacks are only targeted towards specific executives within a firm. Attackers utilize this personalized approach with the goal of gaining access to financial information and personal information of executives, employees, and the company for malicious reasons. The phishing attempts are sophisticated and therefore can be hard to recognize as malicious.

Attackers may use several techniques to target a company’s executive, including:
- Business email compromise (BEC)
- Taking over a compromised corporate email address
- Credential phishing
- Stealing login credentials to access internal servers
- Smishing
- Utilizing links over SMS that are infected with malware
- Vishing
- Eliciting information or influencing action over a phone call
Whaling attacks are distinguished from other phishing attempts by the personalized nature of the attacks. The emails are specifically targeted and geared towards a high-level executive. Whaling is characterized by:
- The attacker spending lots of effort to make the attack very personalized in a high-investment/high reward attempt
- The attacker conducting background research using social media/other publicly available info about the person to increase "authenticity" of the phish
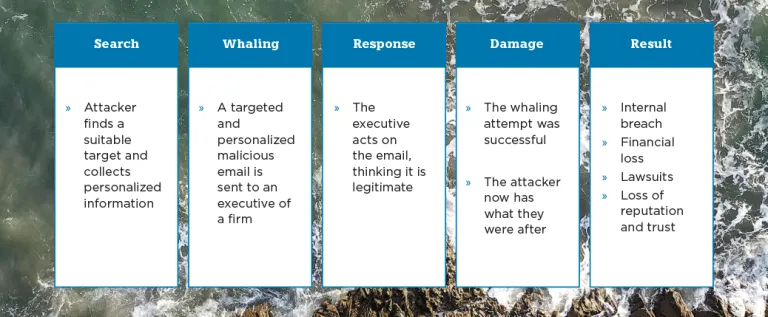
One of the most recent examples of whaling attacks includes former Australian hedge fund Levitas Capital. The fund was hit with an attack in November 2020, after one of the co-founders clicked on a fake Zoom link. This triggered malicious malware to be released onto the company’s network. Attackers were then able to completely take over the Fund’s email system, allowing them to transfer money and file fraudulent invoices. Only two weeks later did the firm realize they were compromised. As a result, Levitas Capital’s largest institutional client pulled their investment. While the attackers were able to secure $800,000, the reputational damage forced the hedge fund to permanently close.
How can firms help defend themselves against whaling attacks?
Firms can take the following steps to help reduce the likelihood of their executives becoming a victim of a whaling attack:
- Educate senior management, assistants, and helpdesk personnel about the effects of whaling attacks and how to spot them in both their professional and personal lives
- Conduct personalized mock whaling attacks to test C-suite executives regularly
- Maintain private social media profiles for C-suite executives
- Mark external emails that originate outside of the firm
- This reduces the risk of clicking on malicious emails that may look similar to those of internal facing (e.g., external email asking for you to reset an internal password)
- Establish a verification process before transferring funds or sensitive information
- Implement data loss prevention solutions
How should firms respond if their executive has been a victim of a whaling attack?
The incident response plan of a whaling attack is similar to a firm’s incident response plan of any successful phishing attack, however; the level of impact is heightened. If a high-level executive at the firm becomes a victim, the following incident response actions should be taken:
- Triage the incident to identify the potential impact and range of the attack
- How much was the direct monetary loss?
- To what degree is there reputational damage to your firm?
- Has there been or could there be potential data breaches?
- Contact the executives’ private bank and the bank/institution where the firm’s assets are located immediately
- Inform them of the possible transfer in question and provide any other payment details if applicable
- Ask for their intervention in preventing the transfer of funds
- Contact the firm’s legal team
- Inform them of all the facts related to the incident
- Contact law enforcement
- They may be able to freeze and return a firm’s stolen funds
- Brief the board and senior management
- Call an emergency meeting to discuss the incident and further actions that should be taken
- File a complaint with the FTC and FBI’s Internet Crime Complaint Center (IC3)
- Consult an external cyber-forensics firm
- Report the incident to the firm’s cyber-insurance company, if applicable
How can firms report a whaling attempt to officials?
The firm may go to the FTC’s complaint portal to report any phishing attack. In addition, if the firm received a phishing email, they can forward the email to the FTC at spam@uce.gov and to the Anti-Phishing Working Group at reportphishing@apwg.org.
How Aponix® Can Help
ACA Aponix offers the following solutions that can help your financial institution develop, implement, and maintain the required information security program:
- Threat intelligence, Phishing Testing, and Monitoring
- Payment and Fraud Risk Assessment Services
- Penetration Testing and Vulnerability Assessments
- ACA Aponix's PortCo Defend™
- Operational Resilience and Governance


