Highlights from the 2020 NSCP / ACA Aponix Cybersecurity Compliance Programs Survey
Financial services firms today are under almost constant cyber threat. The average cost of a cyber-related data breach now costs $3.86 million according to IBM's 2020 Cost of a Data Breach Report and financial services firms remain a target. In 2019, over 62% of breached data came from financial services.
Benchmarking your firm’s cybersecurity program against those of your peers is a smart way to identify the compliance gaps your firm should address. ACA Aponix recently partnered with the National Society of Compliance Professionals (NSCP) to conduct our third 2020 NSCP / ACA Aponix Cybersecurity Compliance Programs Survey. The goal of the survey, which received 160 responses this year, is to provide financial service firms the opportunity to gain insight into cybersecurity compliance programs across the industry.
Cybersecurity is a Serious Risk to All Firms
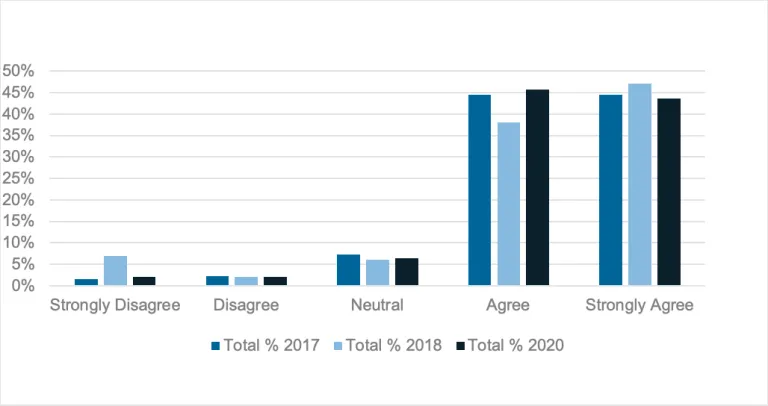
Not surprisingly, 95% of the survey’s respondents agree that cybersecurity concerns are a serious risk.
Survey Question: Do you believe cybersecurity concerns are a serious risk to your business?
Full Survey Report
In our report, The State of Cybersecurity for Financial Services Firms: Results and Analysis from the 2020 NSCP/ACA Aponix Cybersecurity Compliance Programs Survey, we dive deeper into the results and provide actionable guidance from the survey responses. The report covers a variety of cybersecurity themes including staffing, testing, vendors, cloud usage, and more.
Watch the Webcast
Watch our on demand webcast where we discussed the results of this survey, how these results compare with the results of previous surveys, and recommended steps for further action.
If you have any questions, please contact your ACA Aponix consultant or email us at info@acaaponix.com.
How ACA Can Help
ACA Aponix offers the following solutions that can help protect your firm from vulnerabilities and related cybersecurity risk, including:
- Cybersecurity and technology risk assessments
- Vendor diligence and management
- Penetration testing and vulnerability assessments
- Policies, procedures, and governance
- Threat intelligence
- Mock regulatory cybersecurity exams


