Firms Receive Phishing Attempts From False FINRA and SIPC Domains
On June 16th, ACA confirmed several firms received a wave of phishing emails from fake FINRA and SIPC email domains. While the scope of these attacks is still unclear, firms should be on the lookout for potential phishing attacks, disguised as messages from FINRA, SIPC and/or other regulatory agencies.
Red Flags
These phishing emails are arriving from the impersonated domains “@firms-finra.org” and “firms-sipc.org”.
FINRA’s real domain is “@finra.org” while SIPC’s real domain is “@sipc.org”. In addition, they include bogus call-back numbers that may result in busy signals or connecting to a false FINRA representative. This set of emails also utilizes the name of the victim’s firm in the subject line. It is important to note that these emails may use the names of legitimate FINRA and SIPC employees, but that the emails are connected to threat actors.
Below is a sample phishing email in circulation:
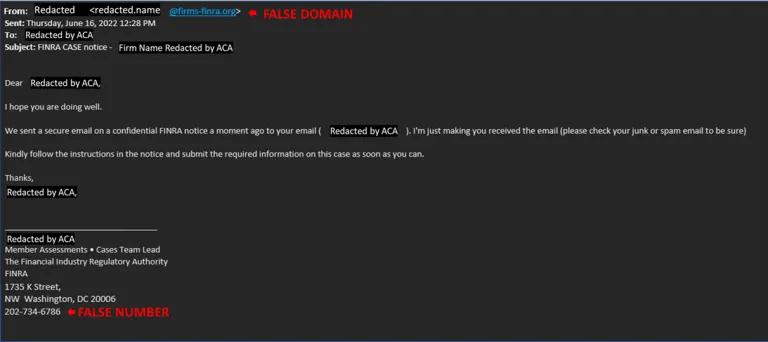
Immediate Action
Threat actors often capitalize on emails from regulatory bodies elicit swift action from recipients. Because of this, firms should ensure their employees are made aware of the threat as soon as possible and are equipped to react appropriately. If an employee receives a suspicious email from a domain they suspect may be masquerading as a regulator, we recommend the following actions:
- Do not click any links in the email or open any attachments. Immediately escalate the issue to the firm’s IT team.
- Confirm the validity of the email by conducting a call-back to a trusted contact at FINRA or using the phone number listed directly on their FINRA and SIPC's website. If the firm does not have a trusted contact at FINRA or SIPC, reach out and establish contact with the regulatory body, as well as alert them to the fraud.
- Reach out to trusted cyber advisors and alert them to the fraud.
- Alert all employees of ongoing phishing attempts, educating them on what to look for (e.g., legitimate domains), who they should reach out to internally, and how to safely dispose of the email (e.g., reporting to IT and/or holding SHIFT + Delete).
Our Guidance
According to the 2022 Data Breach Investigations Report from Verizon, 82% of breaches are a result of a human element, and 41% of business email compromise involved phishing. It is crucial to educate employees on the dangers of phishing attempts, as well as the precautions they ought to take:
- Never trust the “From” field in an email
- Do not download attachments from an unsolicited source
- Be cautious of alarmist email subject lines (e.g., “urgent”, “transfer”, “request”, etc.)
- Create bookmarks for frequently visited websites to avoid visiting fake websites
- Contact the IT department when in doubt of unknown and suspicious links
- Validate email requests with callbacks to a contact you have on file, or visit a legitimate website to find a callback number
For more guidance on impersonated domains, click here to read our advice.
How We Help
We provide services to help organizations tackle threats such as phishing:
- Staff security training to educate all staff on industry best practices, cyber trends, and emerging threats.
- Phishing testing to deploy a targeted email campaign to test employees’ ability to identify and handle phishing threats.
- Penetration testing and vulnerability assessments to identify network vulnerabilities that can help reduce the risk of a breach and associated financial, operational, and reputational losses.
Learn more about our additional solutions here.
For questions about this alert, or to find out how we can help you meet your regulatory cybersecurity obligations, please reach out to your trusted cyber advisor or contact us.


